Interest in Red Teaming is growing. More and more security leaders are hearing the term “Red Teaming” without fully understanding what it involves or why it is highly relevant. News of data breaches, often through supply‑chain compromises or ransomware attacks, is creating unease, while standard risk assessments can feel overly theoretical.
Red Teaming offers a practical way to understand how attackers operate and how well an organisation withstands genuine pressure.
By measuring how your organisation responds to a realistic attack, you can boost resilience and base your security investments on hard evidence rather than on gut feeling or assumptions.
What Is Red Teaming?
Red Teaming is a comprehensive security exercise in which ethical specialists simulate genuine attackers. The process reveals how security measures, processes, and people perform under pressure. It maps potential attack paths that could lead to data breaches and operational disruption. This is particularly relevant for organisations for organisations that have their basic security in order, carry out regular penetration tests, and want to take the next step.
Red Team vs Blue Team vs White Team
Where the Red Team launches the attack, the Blue Team forms the defence, made up of the organisation’s own security personnel. Their task is to detect and neutralise the attack as quickly as possible.
Then there’s the White Team, the only individuals within the client organisation who know in advance that the test will take place. Usually limited to a maximum of three people, ideally the CISO and a board member, the White Team safeguards confidentiality, manages internal coordination, and ensures the Red Teaming engagement runs smoothly.
How a Red Team Operation Unfolds
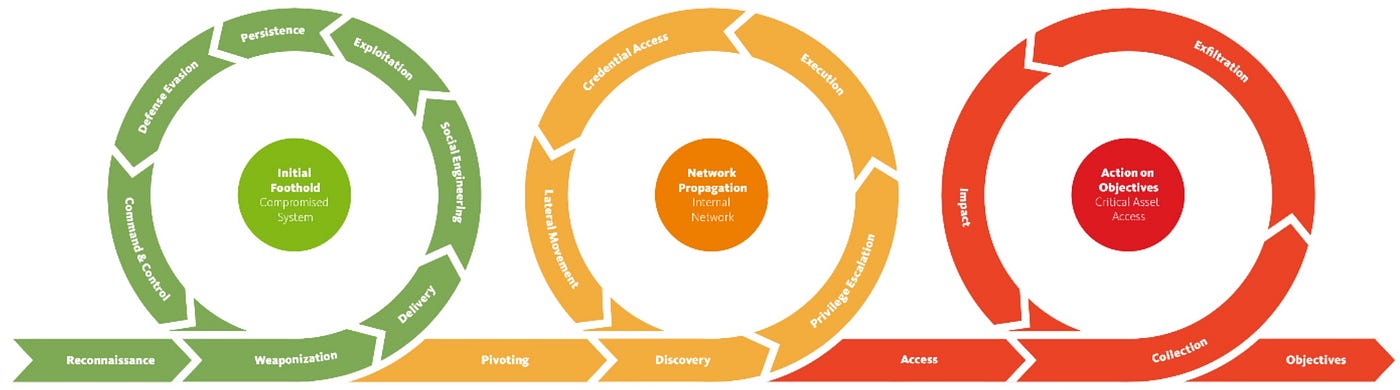
Every operation begins with a tightly‑structured test plan comprising multiple scenarios. In collaboration with the client’s White Team, we determine the sequence of these scenarios and follow the Unified Kill Chain methodology:
Initial Foothold (IN): Gaining initial access via methods such as phishing, exploiting vulnerabilities in external systems, or leveraging leaked credentials.
Network Propagation (THROUGH): Expanding within the network, obtaining additional accounts, elevating privileges, and establishing multiple access points.
Action on Objectives (OUT): Achieving the simulated goal - carefully and often in consultation with the White Team - sometimes introducing deliberate “noise” to test the Blue Team’s response effectiveness.
Reporting: Documenting all actions and findings, including detections by the Blue Team, and translating them into concrete, prioritised improvements.
A successful exercise hinges on clear organisational alignment. Thorough preparation safeguards business continuity and security throughout the engagement. The test plan details all identified risks and the mitigation measures in place. At every stage of the Red Team phase, we strike a balance: progressing efficiently while ensuring all actions are carefully considered and cause no unnecessary damage.
What Does the Team Look Like?
At Securify, a typical Red Team includes:
- Red Team Lead: Oversees the engagement, serves as the primary contact for the client’s White Team, and holds ultimate responsibility for all technical actions.
- OSINT Specialist: Collects and consolidates publicly available and leaked information to help plan attack scenarios.
- Initial Entry Specialist: Focuses on gaining that first foothold through digital and physical social engineering attacks.
- Operator: Expands the attack post‑entry, moves through networks, and evades detection systems.
- Support: Provides specialist assistance on demand, such as developing or customising malware for specific attack scenarios.
Types of Red Teaming
A wide range of Red Teaming approaches exists. At Securify, we offer the following options:
ART test
The ART (Advanced Red Teaming) test follows the framework of the Dutch Central Bank (DNB). It simulates the methods of established hacker groups using threats relevant to the sector. This controlled attack targets a pre‑defined objective based on sector‑specific threat intelligence.
TIBER test
Threat Intelligence‑Based Ethical Red Teaming (TIBER) is designed for financial institutions, including banks, payment providers, pension administrators, and insurers. The test comprises three distinct scenarios, each built around sector‑relevant threat intelligence.
ZORRO test
The ZORRO test focuses on Red Teaming within the healthcare sector. Conducted under the DNB’s ART framework with Z‑CERT as the facilitating body, it uses sector‑specific threat intelligence to perform a controlled attack on a defined target, assessing the resilience of systems and processes.
DORA‑TLTP test
Threat‑Led Penetration Testing (TLTP) falls under the EU’s Digital Operational Resilience Act (DORA) and applies to financial institutions. This methodology employs sector‑specific threat intelligence to execute a controlled attack against a defined objective. Following scenario completion, Purple Teaming is mandatory, allowing offensive and defensive teams to jointly evaluate attack techniques and defence measures.
Tangible Outcomes of Red Teaming
Red Teaming delivers measurable insights that guide strategic security investments. Key outcomes include:
- Clear visibility of attack paths: The exercise shows how attackers navigate infrastructure, processes, and human factors.
- Evidence‑based prioritisation: Findings pinpoint which measures are effective and which areas require attention.
- Validation of detection and response: Security teams see how monitoring tools, incident processes, and decision‑making withstand realistic pressure.
- Enhanced resilience: Organisations become familiar with adversary behaviours and improve readiness for future incidents.
These insights enable leadership to make well‑informed, evidence‑driven security decisions.
Turning Red Team Results into Immediate Progress
At Securify, every Red Teaming engagement concludes with a replay and a Purple Teaming session. Together with the Blue Team, we revisit the attack scenarios, sharing knowledge and identifying lessons learned. This empowers the internal security team to implement remediation steps immediately and strengthen resilience.
By gathering the Blue Team’s questions and learning goals in advance, we ensure these sessions are highly relevant and directly actionable.
In the visual below, you can see feedback from a client’s Blue Team on malware developed by the Securify Red Team during a TIBER test. Feedback that described the team as a “Nation State Actor”, a label we take great pride in.

Would you like to learn more about Red Teaming, or explore how Securify can assess and strengthen your organisation’s resilience? Get in touch with us today.